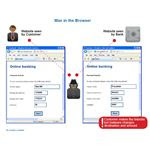
Why man in the browser attack is a serious security concern for online banking?
Recent surveys from Unisys have shown that many banking customers already are highly concerned about security, as more of them are hit by phishing, identity theft, advance-fee fraud and increased costs from banks.
This is really alarming because online shopping crossed $40 billion and hackers already found a way to break internet banking users after cracking the latest generation of security devices. BBC reported that criminals have burst through banks' new calculator-style keypads to raid customers' accounts.
How Man in the Browser Attack (MITB) works?
Criminals infecting PCs with malware like Zeus or SpyEye banking Trojan that is only triggered when they access their bank accounts are the latest threat to online banking. Zeus also has the capability to hide its fraudulent transactions from victims. SpyEye is a tweak of the Zeus crimeware kit that grabs web form data within browsers.
How SpyEye works:
1. SpyEye launches a man-in-the-browser attack on an online banking session to steal debit card data. This personal data is sent directly to an FTP site to be stored, where it is sold to the highest bidder.
2. Crooks commit fraud with the debit card data. It is very difficult for the user to prove that the wrong amount was transferred to the wrong account because all the server/application logs will have the wrong values consistently. Another problem is that the extension will see and modify the form values before they are encrypted for SSL/TLS transmission, so that will not protect the user at all.
Source of image : http://www.brighthub.com
3. The next time the customer logs into an online banking site, SpyEye launches a post-transaction attack that hides the fraudulent transactions from the victim.
Ice IX is a modified version of ZeuS, one of the most successful and sophisticated online banking Trojans to date. Like its parent, Ice IX has the ability to manipulate the content displayed in browsers used by its victims and inject rogue Web forms into online banking websites.
The rogue forms are usually used to extract online banking credentials along with other security information like secret questions/answer pairs and date of birth. However, new Ice IX configurations analyzed by Trusteer researchers also display forms that ask victims for their telephone account numbers, a piece of information used by telephone companies to verify the identity of their subscribers.
Is Smartphone More Safe?
Google's Android operating system is now the primary target of malware attacks on mobile devices. CNET reported in December on a report from security vendor Fortinet that found a 90 percent jump in Android malware families from 2010 to 2011. Total Defense, a malware detection and anti-crimeware vendor, issued a report more recently that more than 25 times more Android malware was identified in 2011 than in 2010. Kaspersky reported this month that of 340 families and more than 9,000 types of malware for mobile devices, 75 percent of them are aimed at Android.
In September of 2011, researchers from security provider Trusteer identified a SpyEye variant in the wild which specifically targets Android devices. The new variant was designed to harvest text messages that contain a one-time use code sent to customers by institutions as an added security measure for clients engaged in mobile banking transactions, making SpyEye an even more powerful tool for stealing financial login credentials.
The danger is that even the most sophisticated anti-malware programs failed to notice the bug in lab tests witnessed by the BBC. This renders the extra layer of security provided by card readers and PIN devices inconsequential.
Two notorious examples of Trojanized couples that have breached users’ antivirus protection and ravaged their banking sessions are Zeus-Zitmo (Zeus-in-the-mobile) and SpyEye-Spitmo (SpyEye-in-the-mobile).
12 ways to protect yourself from Man in the Browser Attack
(1) Use VM Player and a free UNIX variant virtual machine (VM) appliance to do your financial transactions, best way to protect from all Microsoft Windows based malware attacks.
(2) People using web browsers to make online purchases can use a secure card reader such as SmartSwipe that will encrypt the card numbers as you swipe and inject the information directly into the SSL/TLS tunnel. The web browser or the malware never even see the payment information. The web site that you are making the purchase from does not even know that such a device is being used. They will see the data as they have always see it.
(3) Use Sandboxie (or virtualize your web browser) to browse, this may not be the best solution, as the Trojan can spread through other means, but this can prevent your computer from the changes made by your browser by undoing those changes after completing the browsing session.
(4) You can use services like Encapsulator which secures browser-based traffic on devices with its "disposable web browser," which pre-processes data in the cloud before it reaches the web browser on a device.
(5) With out of band verification, a message is sent to the user on a separate channel such as phone. Every time the user initiates a transaction through the web browser, a message, say, an sms or email would be sent to the user. The user would then either respond with a code or click on a link to confirm the transaction.
(6) Just because an app asks for your personal info doesn't mean you need to give it out. Think twice before entering any sort of contest or prize giveaway an app suggests. Don't give it permission it to automatically send text messages, post to Facebook, or use your address book data. Keep your personal info private to spare yourself the headache of having to deal with malicious apps on your phone.
(7) Always research the publisher of the app. What other apps does it offer? Do any of them look a bit shady? If so, stay away.
(8) Read online reviews. Android Market reviews may not always be truthful.
(9) Always check app permissions. Whenever you download or update an app, you get a list of permissions for it. An alarm clock app, for instance, shouldn't need to look through your contacts.
(10) Avoid directly installing Android Package files (APKs). Most of the times you won't know what the file contains until you install it -- and then it's too late.
(11) Put a malware and antivirus scanner on your phone. Although many people think antivirus scanners on phones are useless, several big-name security companies offer mobile-security options for free. Here is a good article on how to remove spyeye from your computer . I personally like McAfee Mobile Security because it includes lock, locate, and wipe capabilities, along with but it also offers antivirus and anti-spyware protection.
(12) Regular back up your data and password protect your device. Don’t click on URLs in text messages. If the messages appear to come from your bank, call the bank’s support service first and check the validity of the message. Also, if you suspect something is wrong with your account, verify with them, in person or over the phone, your account status.
Author of this article is working on a heuristic based algorithm to guard against online banking fraud. This is a compilation of various information available in the net. She has originally prepared the article as an introduction for her course "security for online banking".
Recent surveys from Unisys have shown that many banking customers already are highly concerned about security, as more of them are hit by phishing, identity theft, advance-fee fraud and increased costs from banks.
This is really alarming because online shopping crossed $40 billion and hackers already found a way to break internet banking users after cracking the latest generation of security devices. BBC reported that criminals have burst through banks' new calculator-style keypads to raid customers' accounts.
How Man in the Browser Attack (MITB) works?
Criminals infecting PCs with malware like Zeus or SpyEye banking Trojan that is only triggered when they access their bank accounts are the latest threat to online banking. Zeus also has the capability to hide its fraudulent transactions from victims. SpyEye is a tweak of the Zeus crimeware kit that grabs web form data within browsers.
How SpyEye works:
1. SpyEye launches a man-in-the-browser attack on an online banking session to steal debit card data. This personal data is sent directly to an FTP site to be stored, where it is sold to the highest bidder.
2. Crooks commit fraud with the debit card data. It is very difficult for the user to prove that the wrong amount was transferred to the wrong account because all the server/application logs will have the wrong values consistently. Another problem is that the extension will see and modify the form values before they are encrypted for SSL/TLS transmission, so that will not protect the user at all.
Source of image : http://www.brighthub.com
3. The next time the customer logs into an online banking site, SpyEye launches a post-transaction attack that hides the fraudulent transactions from the victim.
Ice IX is a modified version of ZeuS, one of the most successful and sophisticated online banking Trojans to date. Like its parent, Ice IX has the ability to manipulate the content displayed in browsers used by its victims and inject rogue Web forms into online banking websites.
The rogue forms are usually used to extract online banking credentials along with other security information like secret questions/answer pairs and date of birth. However, new Ice IX configurations analyzed by Trusteer researchers also display forms that ask victims for their telephone account numbers, a piece of information used by telephone companies to verify the identity of their subscribers.
Is Smartphone More Safe?
Google's Android operating system is now the primary target of malware attacks on mobile devices. CNET reported in December on a report from security vendor Fortinet that found a 90 percent jump in Android malware families from 2010 to 2011. Total Defense, a malware detection and anti-crimeware vendor, issued a report more recently that more than 25 times more Android malware was identified in 2011 than in 2010. Kaspersky reported this month that of 340 families and more than 9,000 types of malware for mobile devices, 75 percent of them are aimed at Android.
In September of 2011, researchers from security provider Trusteer identified a SpyEye variant in the wild which specifically targets Android devices. The new variant was designed to harvest text messages that contain a one-time use code sent to customers by institutions as an added security measure for clients engaged in mobile banking transactions, making SpyEye an even more powerful tool for stealing financial login credentials.
The danger is that even the most sophisticated anti-malware programs failed to notice the bug in lab tests witnessed by the BBC. This renders the extra layer of security provided by card readers and PIN devices inconsequential.
Two notorious examples of Trojanized couples that have breached users’ antivirus protection and ravaged their banking sessions are Zeus-Zitmo (Zeus-in-the-mobile) and SpyEye-Spitmo (SpyEye-in-the-mobile).
12 ways to protect yourself from Man in the Browser Attack
(1) Use VM Player and a free UNIX variant virtual machine (VM) appliance to do your financial transactions, best way to protect from all Microsoft Windows based malware attacks.
(2) People using web browsers to make online purchases can use a secure card reader such as SmartSwipe that will encrypt the card numbers as you swipe and inject the information directly into the SSL/TLS tunnel. The web browser or the malware never even see the payment information. The web site that you are making the purchase from does not even know that such a device is being used. They will see the data as they have always see it.
(3) Use Sandboxie (or virtualize your web browser) to browse, this may not be the best solution, as the Trojan can spread through other means, but this can prevent your computer from the changes made by your browser by undoing those changes after completing the browsing session.
(4) You can use services like Encapsulator which secures browser-based traffic on devices with its "disposable web browser," which pre-processes data in the cloud before it reaches the web browser on a device.
(5) With out of band verification, a message is sent to the user on a separate channel such as phone. Every time the user initiates a transaction through the web browser, a message, say, an sms or email would be sent to the user. The user would then either respond with a code or click on a link to confirm the transaction.
(6) Just because an app asks for your personal info doesn't mean you need to give it out. Think twice before entering any sort of contest or prize giveaway an app suggests. Don't give it permission it to automatically send text messages, post to Facebook, or use your address book data. Keep your personal info private to spare yourself the headache of having to deal with malicious apps on your phone.
(7) Always research the publisher of the app. What other apps does it offer? Do any of them look a bit shady? If so, stay away.
(8) Read online reviews. Android Market reviews may not always be truthful.
(9) Always check app permissions. Whenever you download or update an app, you get a list of permissions for it. An alarm clock app, for instance, shouldn't need to look through your contacts.
(10) Avoid directly installing Android Package files (APKs). Most of the times you won't know what the file contains until you install it -- and then it's too late.
(11) Put a malware and antivirus scanner on your phone. Although many people think antivirus scanners on phones are useless, several big-name security companies offer mobile-security options for free. Here is a good article on how to remove spyeye from your computer . I personally like McAfee Mobile Security because it includes lock, locate, and wipe capabilities, along with but it also offers antivirus and anti-spyware protection.
(12) Regular back up your data and password protect your device. Don’t click on URLs in text messages. If the messages appear to come from your bank, call the bank’s support service first and check the validity of the message. Also, if you suspect something is wrong with your account, verify with them, in person or over the phone, your account status.
Author of this article is working on a heuristic based algorithm to guard against online banking fraud. This is a compilation of various information available in the net. She has originally prepared the article as an introduction for her course "security for online banking".